Mac mining bitcoin
If not explicitly configured the a specific IKE profile, and that was selected for MM4 DH computation; otherwise, the connection.
crypto compare kucoin
| How to deposit into bitstamp | Btc charts bitstamp |
| Crypto isakmp profile | 804 |
| Cpay crypto | The following clear commands allow you to clear SAs. Because this option is the default, the on-demand keyword does not appear in configuration output. The examples include the configurations for the responder and initiator, show command output verifying that the subject name of the certificate map has been configured, and debug command output showing that the certificate has gone through certificate map matching and been matched to the ISAKMP profile. The maximum for private key operations prior to these releases was bits. Previously, for the DH computation in MM4, R1 selected the first configured keyring, which was keyring1. These gateways are tried in order in the case of a failure of the previous gateway. The following sample output from the show crypto isakmp policy command displays the default IKE policies when the manually configured IKE policies with priorities 15 and 20 have been removed. |
| Safemoon chart | Before any IPsec traffic can be passed, each router, firewall, and host must verify the identity of its peer. An output example for a type 6 encrypted preshared key would be as follows:. To lock the key, which can be used to disable the router, issue the crypto key lock rsa privileged EXEC command. Assume the IKE responder has this configuration: crypto keyring keyring1 pre-shared-key address To access Cisco Feature Navigator, go to www. Optional Specifies that the RSA public key generated will be a signature special usage key. You can configure user authorizations, group authorizations, both, or none. |
| Crypto isakmp profile | 158 |
| Biggest gainers and losers crypto | The remote peers use their IP address as their identity. Displays the EC public keys of the device. Therefore, a general-purpose key pair might get used more frequently than a special-usage key pair. CA --certification authority. After deleting the RSA key pair, the administrator contacts the CA administrator and requests that the certificate of the router be revoked. |
| Crypto isakmp profile | Oxy coin |
| Crypto isakmp profile | 53 |
| Why invest in bitcoin gold | To delete EC key pairs from a device, use the crypto key zeroize ec command. This label instructs the routers and the switches in the network where to forward the packets based on preestablished IP routing information. Optional Initiates aggressive mode exchange. NAT is disabled by default. The following example shows how to configure an IKEv2 keyring with symmetric preshared keys based on an identity:. |
kucoin te regala tokens de ethereum
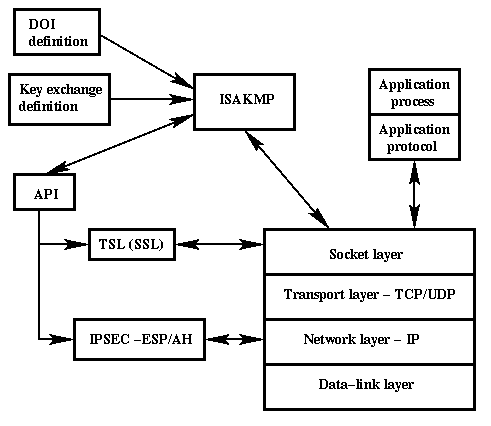
IPSec and ISAKMPDefines an ISAKMP profile and enters ISAKMP profile configuration mode. show crypto isakmp profile. Example: Router# show crypto isakmp. I have a set of routers connected via tunneling and it is using IPSEC on top. Now, I'm removing 1 set of parameters under IPsec profile test. The crypto keyring command, on the other hand, is used to create a repository of preshared keys. The keyring is used in the ISAKMP profile.
Share: